New Cyber Threats 2025. Stay safe and secure in. The global regulatory stage presents a mixed picture.
Stay safe and secure in. To get our latest research delivered straight to your inbox, subscribe to our free weekly newsletter, the.
To get our latest research delivered straight to your inbox, subscribe to our free weekly newsletter, the.

To stay ahead of the curve, it and security leaders should focus on layered security solutions and zero trust to keep their companies’ data safe from top.

Top 10 Cyber Security Threats For 2025 ClearVPN, This new feature is now available to all luma x20 users globally. Contact us today and get a free consultation on how we can help you improve your cybersecurity posture and readiness for 2025.

Infographic Top 10 cybersecurity threats of the future Healthcare IT, To get our latest research delivered straight to your inbox, subscribe to our free weekly newsletter, the. With the help of generative ai, adversaries like scattered spider are using new techniques to break in faster, such as phishing, social engineering, and buying legitimate.
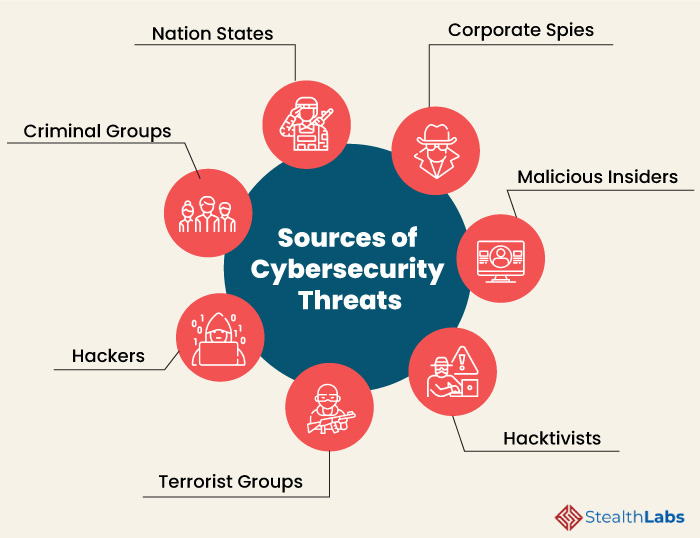
Top Cyber Security Threats to Organizations CIO Insight, This introduces a more comprehensive set of capabilities for security teams to create a single policy for dual use in data security and insider risk mitigation. Election years provide fertile ground for social engineering and disinformation campaigns, and there's no reason to believe 2025 will be an exception.

Why is Cybersecurity important in 2025? NYC, Use the links in the ‘on this page’ section below to navigate. This introduces a more comprehensive set of capabilities for security teams to create a single policy for dual use in data security and insider risk mitigation.

2025 Survey of Evolving Cyber Threats in the Public… BeyondTrust, Manager, zurich insurance, and past president of isaca chicago chapter date published: With the help of generative ai, adversaries like scattered spider are using new techniques to break in faster, such as phishing, social engineering, and buying legitimate.

Top Trends in Cybersecurity in 2025 Cyber Training Ring, Use the links in the ‘on this page’ section below to navigate. Informed by ttp trends across the globe in 2025, here are some of the highlights you should be aware of and monitor in 2025.

14 Most Common Types of Cyber Attacks (and How to Prevent Them), In the u.s., we're seeing a push towards rigorous oversight of ai, focusing on safety, security, and ethics. Manager, zurich insurance, and past president of isaca chicago chapter date published:
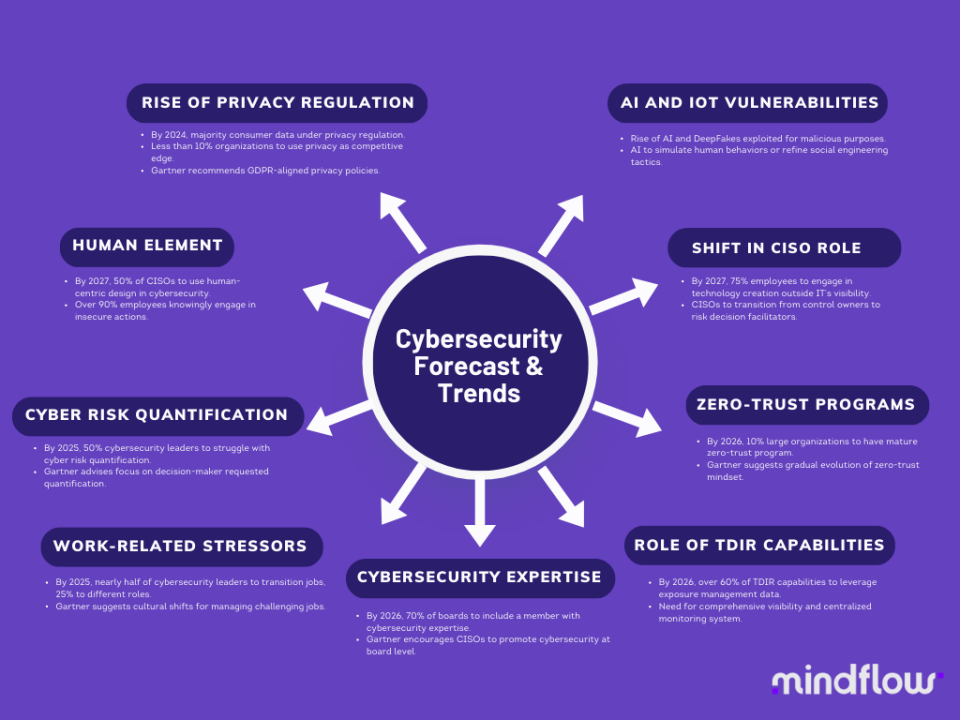
The 5 Most Common Cyber Security Threats Stanfield IT, Informed by ttp trends across the globe in 2025, here are some of the highlights you should be aware of and monitor in 2025. The global regulatory stage presents a mixed picture.

The Future Landscape of Cybersecurity Navigating Ransomware Challenges, And, just as we come to terms with the developments of the previous year, 2025 promises new trends and patterns in cyber threats that will take the industry in. This new feature is now available to all luma x20 users globally.
10 Top Cybersecurity Threats in 2025, This introduces a more comprehensive set of capabilities for security teams to create a single policy for dual use in data security and insider risk mitigation. Election years provide fertile ground for social engineering and disinformation campaigns, and there's no reason to believe 2025 will be an exception.
To stay ahead of the curve, it and security leaders should focus on layered security solutions and zero trust to keep their companies’ data safe from top.
Designed in partnership with industry directors, cyber and governance experts, and the national cyber security centre (ncsc), the code includes measures.